A Reasonable Approach
to Cyber Compliance
A Reasonable Approach to Cyber
Security Compliance Risk Management
Home4

Practical Strategies, Rooted In Reality.
Organizations with limited technical staff and resources often can’t employ the same approach to advanced cybersecurity concepts and requirements that enterprise firms can. Unfortunately, the vast majority of resources to guide and manage these projects are designed for enterprise clients and don’t scale down to help smaller organizations.
Many small and mid-size organizations’ first encounter with cybersecurity frameworks and standards comes from a legal or regulatory obligation.
We can help de-mystify these requirements, give you strategies and options to meet them based on your specific circumstances, and put you on the path to meeting your compliance obligations.
Beyond compliance, we can help you implement a reasonable cybersecurity program geared toward steady improvement over time, and focused addressing your largest business risks first. (This way, you can use your compliance obligations to your long-term benefit
CMMC
Security requirements for DoD contractors
HIPAA
Security requirements for Healthcare
FTC Safeguards
Security requirements for Financial Services
Need a Hand?
The Voice of Experience
Working with hundreds of clients, we’ve developed a basic 4-step process to meet you where you are in your security journey, and help you to the next stage.
Satisfied Clients in More Than 18 States
Satisfied Clients in More Than 11 Countries
Our 4 Step Process
How It Works

Discover
Work with your team to understand where you are and where you need to be, and work with you to create a strategy to get there.

Plan
Craft a process and series of projects to implement your security strategy.


Do
Work with you and your team to get it done.


Review
Tie up loose ends, ensure that the processes you have put in place are followed and working, and determine next steps in your security journey.
Need help designing your Security Program?
Get started with our most popular engagements
Initiating new cybersecurity programs can seem daunting.
We offer Program Kick-Start Services for key cybersecurity functions.
Need help designing your Security Program?
Get started with our most popular engagements.
Popular
Policies & Standards
Your cybersecurity policies and standards should mesh with your compliance requirements.
Popular
Risk Management Program
Risk Management drives security by focusing resources on your largest business risks.
Popular
Vulnerability Management Program
More than patching – prioritize and address vulnerabilities and misconfigurations based on risk.
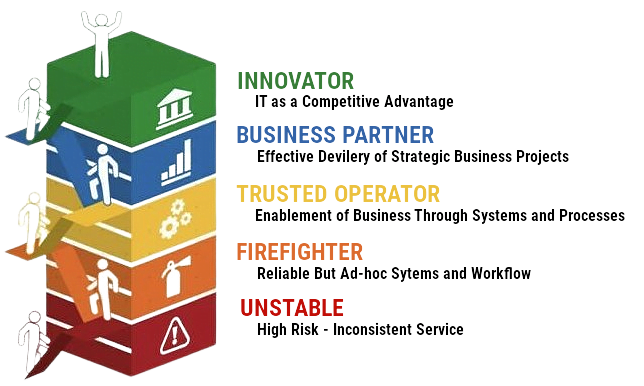
A Trusted Partner
More Than Just Documents and Reports
We don't just tell you what needs to be done, we can help you get it done!
Extensive IT Experience
Our system engineers and network consultants can work with your team to help get you where you need to be.
We Do Not Outsource
We do not resell other companies services, and do not outsource any portion of our services or communications.
E-Verify Employer
All members of our staff are U.S. Citizens and are fully vetted by the E-Verify employment Authorization System.
CJIS Authorized Staff
All members of our staff are CJIS certified, fingerprinted, and have passed law enforcement background checks.
Global Experience
From short and long term consulting projects, to fully managed services, we have satisfied clients in over 18 U.S. States and in over 11 countries.
Are You Comfortable With Your Current Level Of Risk?
IT Management, Governance, and Risk Assessments
-
Vendor Security Assessment
-
Threat and Risk Assessment
-
Internal Controls Self Assessment
-
Service Management Maturity Assessment
-
IT knowledge Transfer Risk Assessment
-
IT Policy, Standards and Procedure Assessment
-
IT Service Desk Maturity Assessment
-
Office 365 Capability Assessment
-
IT Team Effectiveness Assessment
-
Cloud Maturity Assessment
-
Cyber Security Insurance Assessment
-
Vendor Risk Assessment
-
MSP Performance Assessment
We can perform a variety of Assessments to help determine your current risk.
We follow a structured process that includes the following steps:
We follow a structured process that includes the following steps:
Define your appetite: Work with your management or executive team to determine what level of business risk is acceptable for your organization.
Identify the assets: Identify your business processes – and the hardware, software, people and data that are critical to those processes and need to be protected.
Identify the vulnerabilities: Identify the weaknesses in the IT systems, infrastructure and processes that could be exploited by threats such as hackers, viruses, or natural disasters.
Identify the threats: Identify the potential sources of harm to your assets, including external threats such as cyber attacks and internal threats such as employee mistakes or malfeasance.
Analyze the risks: Analyze the likelihood and potential impact of each identified vulnerability and threat.
Evaluate the risks: Evaluate the risks based on the potential impact to the organization and the likelihood of occurrence.
Develop a risk response plan: Based on the risk assessment, develop a plan to address the identified risks, including measures to prevent or mitigate the risks and plans for responding to risks that cannot be eliminated.
Make it a process: Risk assessments should be regularly reviewed and updated to ensure that your organization is adequately protected.
Not Ready For a Full Engagement?
Low Cost Standardized Modules
If you are just getting started, or only need to refresh a few components of your security program, we have a selection of low effort "next steps" to help you get things going.
Not Ready For a Full Engagement?
Low-Cost Standardized Modules
If you are just getting started, or only need to refresh a few components of your security program, we have a selection of low effort "next steps" to help you get things going.
Basic
Risk Appetite
$1,495
- Work with management
- What is risk appetite?
- Risk Pressure exercise.
- Quantitative risk.
- Introduce Risk Register.
Basic Risk Assessment
$4,495
- Identify business processes and assets.
- identify vulnerabilities and threats.
- Assess Risk by impact and likelihood.
- Create Risk Register.
- Create mitigation plans with you.
Basic
Policy, Standard and Procedures Review
$2,495
- Review current policies.
- Compare to compliance needs.
- Evaluate procedures.
- Discuss impact of changes.
- Provide recommendations.
Basic
Business Continuity/DR Review
$2,495
- Business Impact Analysis.
- Identify key applications.
- Review current backup.
- Compare to business needs.
- Provide recommendations.
Basic
Cyber Insurance Review
$1,495
- Review carrier questionnaires.
- Work with your team to respond.
- Recommend key changes.
- Coverage recommendations.
- Review contracts.
Basic
Cyber Hygiene Assessment
$2,495
- Based on CIS Critical Controls.
- Assess basic cyber controls.
- Work with your team.
- Report where you stand.
- Provide recommendations.
Basic Level Assessments Include:
-
Discovery Session
-
Surveys and Data Collection
-
Written Report of Findings
-
Presentation of Findings
-
Implementation Roadmap
-
General Project Plan
A Trusted Partner
When You Need More Than Just
Documents and Reports
About Us
CIS Cyber is the Compliance & Security division of CIS Technical Services Inc. CIS has been providing IT Consulting and Management Services for over 30 years.

CIS CYBER
Contact Info
- 33 Main Street Suite 502
- Nashua, N.H. 03064
Copyright © 2023. All rights reserved.
Contact Info
- 33 Main Street Suite 502
- Nashua, N.H. 03064
Copyright © 2023. All rights reserved.


